You should definitely use Two-Factor Authentication, and there is no excuse not to. Although not perfect, the 2FA is the best option you have to add another level of security to your account. According to Google, research on “How effective is basic account hygiene at preventing hijacking?” using On-device prompt as your Two-Factor Authentication may stop 100% of automated bots and as much as 99% of bulk phishing attacks and 90% of targeted attacks.
Those are awe-inspiring numbers, and on their own should be enough to encourage people to use Two-Factor authentication. So there is no question really whether you should use Two-Factor Authentication, the question is which type or a mix of 2FA you should be using.
The research initiated by Google with close cooperation with researchers from New York University and the University of California lasted a year.
The results are clear, employing any device or knowledge-based challenges dramatically increases the security of your account. But this is more generic, and I wanted to find out what are the best options, and which of the 2FA types should be used in conjunction.
Based on these facts, there is no doubt that anyone who relies solely on the password to secure the account should use some form of Two-Factor Authentication.
Our research shows that simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks that occurred during our investigation.
Google
According to Google research, just signing up on your phone or adding a recovery phone can provide a similar level of protection as 2-Step Verification via device-based challenges.
Take a look at the chart below, even the most controversial method of delivering the code to your phone via SMS can stop 100% of Automated bots, 96% of Phishing attacks, and 76% of Targeted attacks.
That`s not bad, considering that SMS authentication is highly criticized due to the lack of encryption while in transit, which may result in a man-in-the-middle attack or even more dangerous SIM-swapping attack.
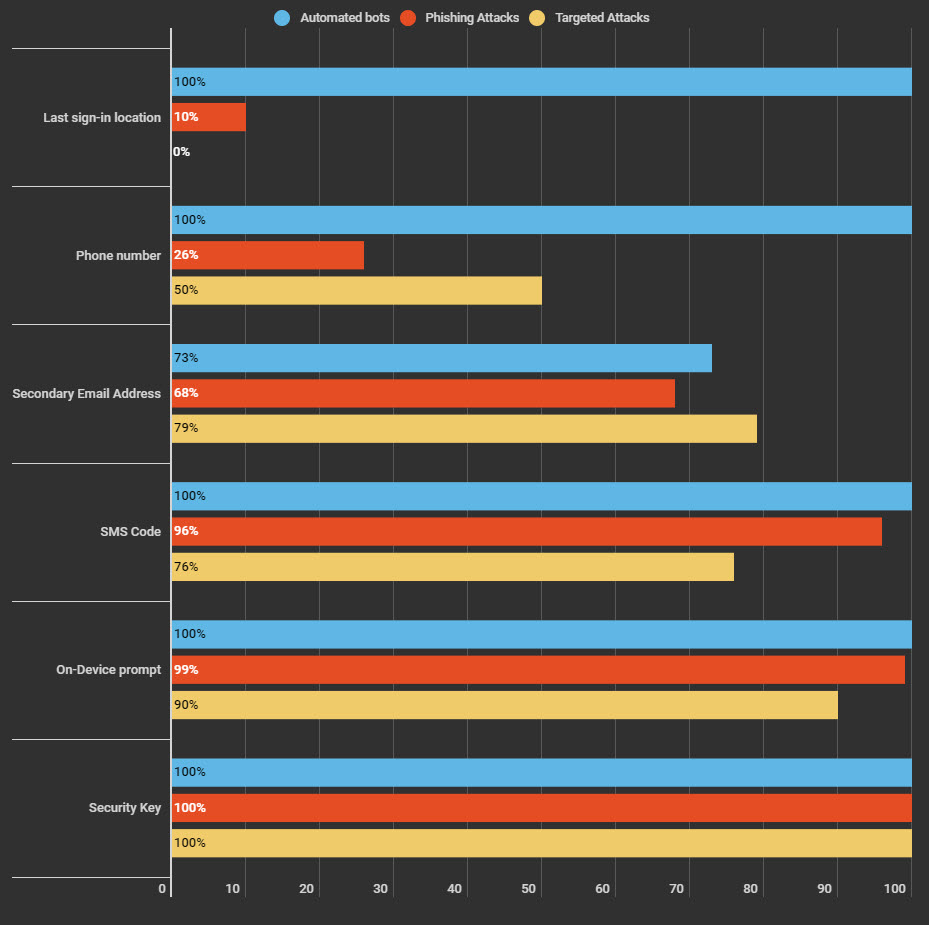
If you like me, and you don`t want to use the SMS Code, try On-Device prompt. Again, check the results of the research in the chart above. The On-Device prompt is the second-best type of verification just behind the Security Key, which so far defended against all three types of attacks.
The On-Device prompt authentication is becoming more popular recently due to the ease of use, especially in industrial/commercial applications. For example, the company I`m working for has just replaced RSA Tokens we have used for a long time with On-Device prompt solution.
It is more convenient for the user just to confirm the login attempt on their phone than perhaps manually typing 6 digit code generated by the Authenticator app or using a physical device like Yubikey every time they are trying to log in.
What is Two-Factor Authentication?
Two-Factor Authentication is a security mechanism that defends against account compromise. Having an account secured with 2FA requires you to authenticate your identity by using a combination of two different authentication factors.
- Something you know.
- Traditionally your password or a PIN code.
- Something you have.
- Such as a phone or a hardware token.
- Something you are.
- Biometrics – your fingerprint for example or an eye iris.
One example of Two-Factor Authentication is the process of withdrawing money from the Cash Machine (ATM). Only the correct combination of a Bank Card (something you have) and a Card PIN (something you know) allows the transaction to be carried out.
The other example relies on the user to present what is called an OTP code or a One-Time Password along with his default password. An OTP code is a one-time use code generated by an authenticator app usually installed on the mobile phone.
Examples of Authenticator applications include Google Authenticator, Microsoft Authenticator, Authy, or Yubico Authenticator, which relies on the Yubikey hardware key to generate the OTP codes.

Most of the well know services including Google, Microsoft or Facebook offers now some optional Two-Factor Authentication to defend against account compromise. Methods such as SMS, TOTP or OTP, or hardware-based code generators require the user to enter a single-use code in addition to their password.
Codes can be sent to the user via a separate channel (SMS for example) or are generated on the fly by the device owned by the user (Google Authenticator app, for example).
Which is the strongest 2FA method?
Once again, according to Google research, the Security Key appears to be the best solution when adding 2FA to your account. However, keep in mind that Security Key is a relatively new technology, and not every service offers this type of 2FA method.
Additionally, this method requires an investment in the physical device, which may cost in the range of $40 to $70 and often requires you to purchase an additional device to use as a backup.
You will then register both Security Keys on the account you would like to protect, and use one of the keys while keeping the other one at home in a safe place.
Personally, I have chosen Yubikey 5C NFC device which offers USB-C and NFC options for a tap-and-go experience.
SMS Code.
Although highly criticized, SMS authentication is still the most commonly used 2FA method. A one-time verification code which typically is a 6 digits long is sent to a user via text message.
It appears to be the most convenient way of second-factor authentication as it does not require any additional software to be installed on the phone.
There is, however, a usability problem that includes delayed delivery or lack of cellular service, and most importantly potential risk of a man-in-the-middle or SIM-swapping attack.
- Potential usability problems.
- Delayed delivery.
- Lack of cellular service.
- Miscopying the code from phone to PC.
- Vulnerability.
- Messages are not encrypted in transit – potential risk of a man-in-the-middle attack.
- SIM-swapping attack.
- Benefits.
- Easy to use, no other software required.
Push or On-Device Prompt.
The user receives a push or on-device prompt on the mobile phone to either approve or deny a login attempt. The On-Device prompt is considered a more secure replacement for SMS method.
- Potential usability problems.
- Requires internet access.
- Device loss.
- Vulnerability.
- Hard to verify due to mostly proprietary authentication methods.
- Benefits.
- No need to retype the code on a computer – user either Approves or Denies a login attempt on a mobile device.
TOTP Code.
For accounts that do not offer authentication using Security Key, this is still my favorite 2FA method. It relies on the service to share a Secret Key with the owner of the account which in turn is used by a third-party application typically installed on a mobile device to generate a 6 or 7 digits code using advanced algorithms.
You may also like: Transfer Google Authenticator 2FA codes to a new phone.
Each code is valid for a set time interval, usually 30 seconds, after which a new code must be generated.
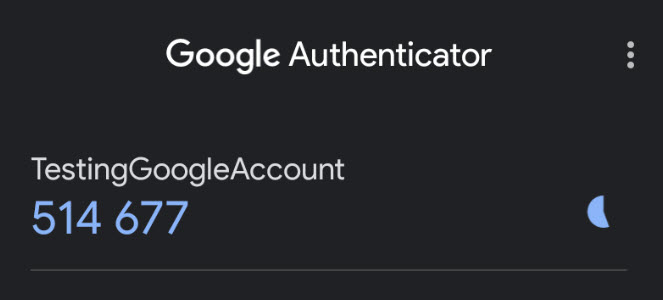
- Potential usability problems.
- 30 seconds window to type the code.
- Miscopying the code from phone to PC.
- Device loss – What if I lose my phone with Google Authenticator on it?.
- Vulnerability.
- Social Engineering – although limited by the set time interval of typically 30 seconds.
- Unsecure Secret Key storage – obtaining Secret Key allows the attacker to generate the TOTP codes.
- Benefits.
- Offered by many services.
- Many Password Managers, including LastPass and 1Password, generate the TOTP codes on the fly.
U2F or Universal 2nd Factor – Security Keys.
Although not as widely available as the methods listed above, this is my absolute favorite choice regarding securing my account with 2FA. The U2F method was initially developed through collaboration with Google and Yubico and now is an open authentication standard that enables internet users to securely access online services with a single physical device instantly and with no drivers or client software required.
The authentication process involves connecting the Security Key to the computer or a mobile device either via USB port or wirelessly via Bluetooth or NFC.

View the list of services that works with Yubikey
- Potential usability problems.
- Expensive – $40 – $70 range for a Yubikey.
- Potential requirement to buy the second device as a backup option.
- Stagnant adoption.
- Vulnerability.
- Benefits.
- According to Google research, the deployment of Security Key was 100% effective in defending against Automated bots, Phishing Attacks and Targeted Attacks.
Which Two-Factor Authentication is best?
That depends on how much risk you are willing to take and what 2FA options are available to you. Let me explain.
The whole idea behind Two-Factor Authentication is to introduce the second step in addition to login and password. That second step as described earlier relies on something you know, something you have, or something you are and as such is often perceived as an inconvenience by the user and may also increase the risk of account lockout.
Google Authenticator method.
Let’s imagine that I have secured my Google account by using Google Authenticator app as my primary and only 2FA method.
You may then ask what will happen if I lose my phone with Google Authenticator on it?
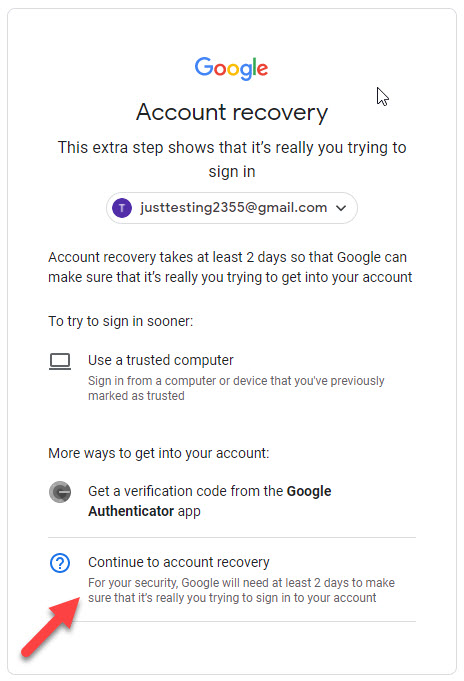
Well, I will have only one option, to use the Google Account Recovery feature which according to Google may take at least 2 days to make sure that it`s really me trying to sign in to my account.
I have never tried the account recovery option before, so I can`t say how effective it is and how long it takes on average to recover the account. But I will guess that it will definitely take longer than 2 days.
If like me, you don`t want to go through the Account Recovery process, make sure to add the recovery phone number and email address to your account. If any of those two options are missing, then during authentication Google may fall back on a weeker knowledge-based challenges.
Those challenges are a problem because phishing pages and targeted attackers can trick you into revealing any additional identifying information Google might ask for.
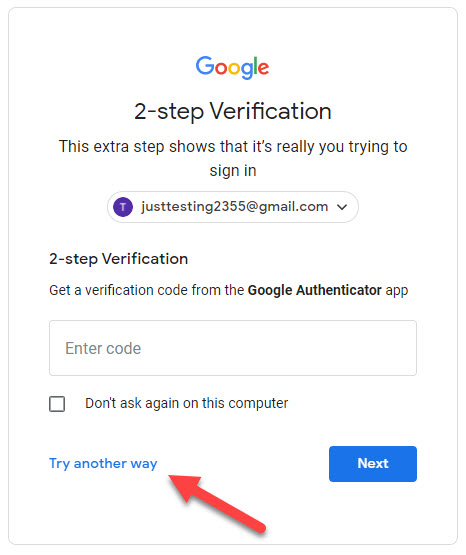
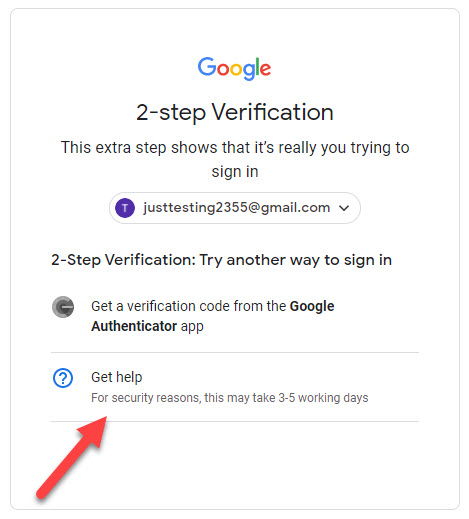
Add more second steps to verify that it’s you.
To counteract the possibility of account lockout, Google encourages users to setup more than one second step to verify that its you in case the other option are not available.
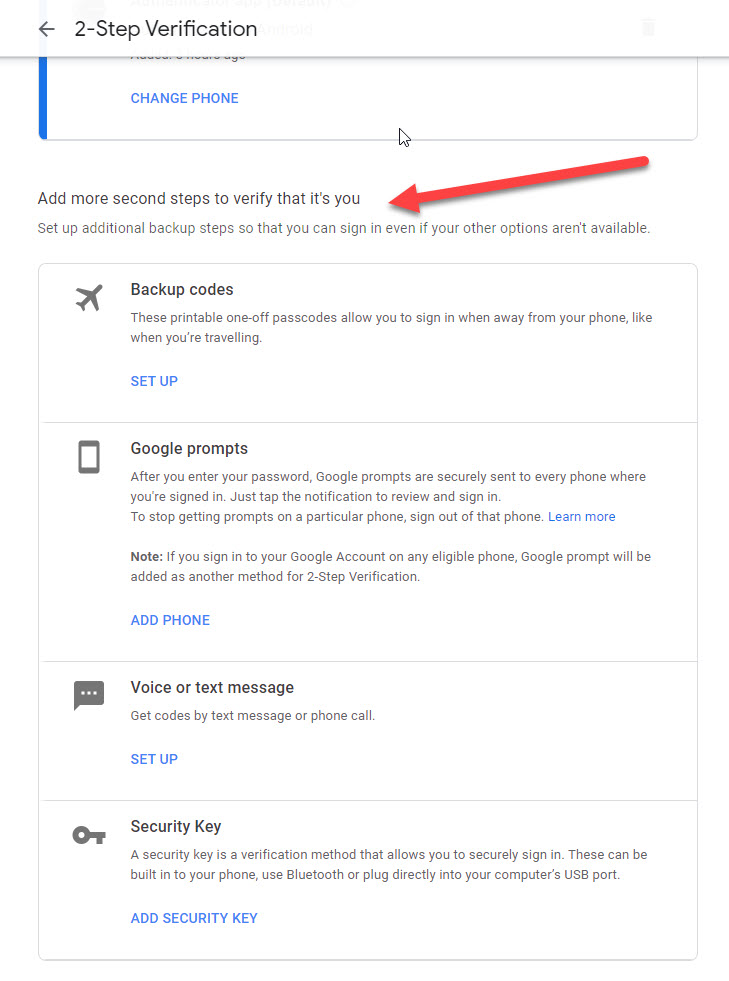
Google Authenticator and Text Message methods.
OK, this time imagine that I have set up two 2FA methods on my account. The primary which is the use of the Google Authenticator app and the secondary as a backup option to request the code via Text message in case I have lost my phone with the Google Authenticator app on it,
What do you think will happen if the attacker, assuming he had your password and login is now faced with Google Authenticator challenge?

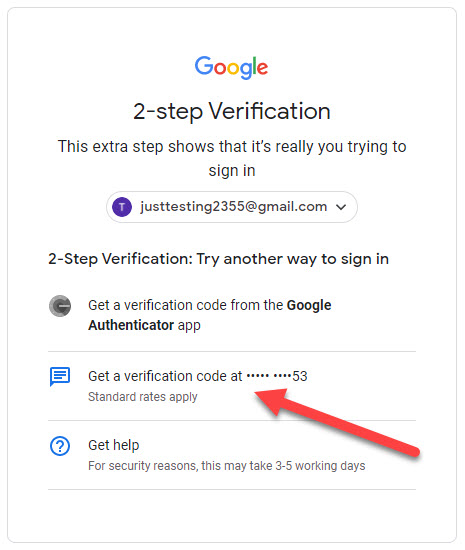
Well, he can click Try another way in the challenge window which will allow him to use the less secured option of requesting the authentication code via SMS message.
And, as we have learned earlier, although better than nothing, the SMS method increases the risk of man-in-the-middle or SIM-swapping attack and generally is being considered as the weakest 2FA method available.
Yubikey 5C NFC Security Key method.
Now let’s try the most secure method using a Security Key. For this example, I will set up my Yubikey 5C NFC hardware key and Text Message as a backup 2FA option.

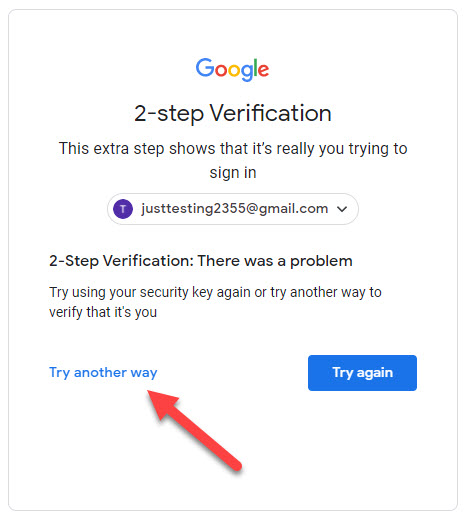
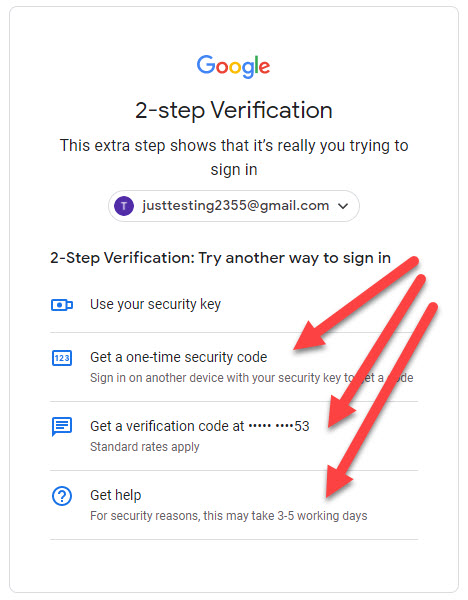
As expected I was able to choose which 2FA option I want to use to log in to my account.
As you can see, the same principle of falling back on the weaker device-based challenge applies. I pretended that I did not have access to my Security Key and opted to try another way. I was then presented with a list of options available to me including the option to request the code via Text message which I have added as a backup.
Don`t be fooled thinking that only because you are using Security Key as the Two-Factor Authentication your account is safe.
That brings me to the main point.
Your account is as secured as the weakest Two-Factor Authentication method you have selected.
Should you use Two-Factor Authentication? Yes, you should, if I haven`t convinced you yet, I don`t know what will. In my mind and according to Google research, any 2FA method is better than relying solely on your login and password, especially if you have a habit of reusing passwords across all your accounts.
I`m not in the position to tell you which 2FA method you should use. You have to decide based on what is available to you, and what backup options you would like to have in case you lose your phone or a Security Key.
I have decided to use Security Key where possible and the Google Authenticator app as a backup option. In most cases, you will be able to set up Google Authenticator app at least and perhaps even the Security Key.
Google Advanced Protection Program.
If you are really worried about your account security, Google offers what is called an Advanced Protection Program which, according to Google, offers stronger security features. For me, however a mere mortal, the standard options are good enough as long as they are applied correctly.
What sites support 2FA?
I can say that probably any reputable website or service offers some Two-Factor Authentication for their users. What type of 2FA may vary and you may need to check with the service or use this quick tool which will allow you to list all 2FA methods offered by the service you would like to use.
